The Evolution of the NIST Cybersecurity Framework (CSF)
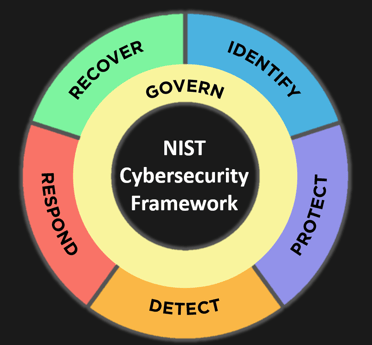
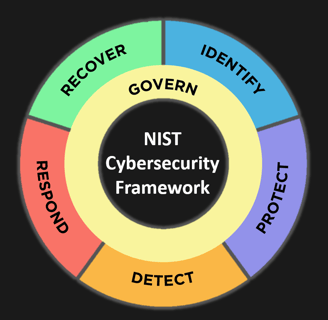
Govern, Identify, Protect , Detect, Respond and Recover
FRAMEWORK

“It is the policy of the United States to enhance the security and resilience of the Nation’s critical infrastructure and to maintain a cyber environment that encourages efficiency, innovation, and economic prosperity while promoting safety, security, business confidentiality, privacy, and civil liberties.”
- Executive Order 13636, February 12, 2013
In 2013, the White House issued Executive Order 13636, urging the National Institute of Standards and Technology (NIST) to craft a comprehensive cybersecurity framework aimed at protecting critical infrastructure. The directive was clear: the U.S. had to bolster its cybersecurity defenses against rising digital threats targeting national security, the economy, and public safety. This led to the development of the NIST Cybersecurity Framework (CSF), a set of voluntary guidelines for organizations, both private and public, to assess, manage, and mitigate cybersecurity risks.
When NIST CSF 1.0 was released in February 2014, it marked a crucial milestone in fortifying critical infrastructure. The framework quickly gained popularity for its flexible, risk-based approach to cybersecurity. It provided a universal language for organizations to evaluate and enhance their cybersecurity posture, with five core functions, Identify, Protect, Detect, Respond, and Recover, serving as the foundation of many organizational strategies.
However, the cybersecurity landscape has evolved drastically since then. The rise of sophisticated cyberattacks, rapid technological progress, and the increasing use of cloud services and hybrid work models have expanded organizations' vulnerabilities. Recognizing this shift, NIST acknowledged that its framework needed to adapt.
Introducing the "Govern" Function
In 2024, NIST unveiled CSF 2.0, which brought a significant update to the framework, introducing a new, sixth core function: Govern. While governance elements had previously existed within the framework, the Govern function now stands as a distinct, formalized core element. This change highlights the growing recognition that cybersecurity is not just a technical concern but a vital component of organizational strategy.
The addition of Govern acknowledges that cyber risk is now integral to enterprise risk management. This necessitates governance to ensure that cybersecurity is aligned with organizational goals, legal requirements, and regulatory expectations. The Govern function in CSF 2.0 stresses the need for senior leaders to actively participate in cybersecurity decision-making.
What Exactly Is the Govern Function?
The Govern function in NIST CSF 2.0 focuses on establishing risk management strategies, policies, and frameworks that integrate cybersecurity into broader organizational governance. This shift underscores the importance of a proactive, risk-driven approach to cybersecurity, ensuring that cybersecurity efforts are in sync with an organization's objectives and risk tolerance.
The Govern function is divided into several key categories to enhance an organization’s ability to manage its cybersecurity posture effectively:
Organizational Context
Understanding the unique context of an organization’s cybersecurity needs, including its mission, stakeholders, and regulatory requirements.Risk Management Strategy
NIST CSF 2.0 stresses the importance of a clear, defined risk management strategy that aligns with the organization’s risk appetite and goals.Roles, Responsibilities, and Authorities
Clarifying roles and responsibilities is crucial for accountability in cybersecurity management. This category ensures that cybersecurity is coordinated and effective across all levels of the organization.Policy
Establishing, communicating, and regularly reviewing cybersecurity policies to keep them relevant and responsive to evolving threats and changes in the organization.Oversight
Ongoing oversight ensures the cybersecurity strategy stays aligned with organizational objectives and that governance practices are updated to meet emerging risks.Cybersecurity Supply Chain Risk Management
Addressing risks associated with third-party vendors and partners, which are increasingly targeted in cyberattacks.
Why the Govern Function Is Critical
The addition of the Govern function underscores the idea that cybersecurity governance is now central to managing digital risks. As cyber threats become more complex, organizations can no longer rely solely on technical solutions. Cybersecurity must now be part of the broader business strategy and governance framework.
By making Govern a core function, NIST highlights the necessity of senior leadership involvement in cybersecurity. In today’s interconnected world, every department, whether finance, operations, or IT, must recognize the cybersecurity risks that can impact their operations. Cybersecurity cannot be isolated in one department; it must be integrated into every part of the organization.
The Govern function also facilitates more informed decision-making, enabling organizations to allocate resources wisely and prioritize cybersecurity efforts based on a clear understanding of their risk exposure.
NIST CSF 2.0 and Zero Trust: A Unified Approach to Cybersecurity
The Zero Trust security model has become a leading approach to cybersecurity in recent years. Based on the principle of "Never Trust, Always Verify" Zero Trust dictates that no user, device, or request should be trusted by defaul, whether they are inside or outside the network perimeter. Instead, every access request is thoroughly verified based on factors such as identity, location, device health, data sensitivity, and anomaly detection. Zero Trust also emphasizes least-privilege access, end-to-end encryption, and continuous monitoring and improvement.
Although the CSF 2.0 and the Zero Trust model may appear to be different, they are, in fact, complementary and can work together. The CSF 2.0 provides a flexible, adaptable framework that supports various cybersecurity models, including Zero Trust. Several of the updates introduced in CSF 2.0 are aligned with Zero Trust principles, such as:
CSF Core Structure Update
CSF 2.0 places a stronger emphasis on identifying and protecting the data, assets, and services that are most critical to the organization. It also focuses on responding to and recovering from incidents affecting these vital elements. This aligns with the Zero Trust concept of defining and securing the "protect surface", the collection of data, applications, assets, and services essential to an organization's mission and objectives. (nist.gov)Implementation Examples
A new element in CSF 2.0 is the Implementation Examples, which offer practical guidance on how to implement Zero Trust architectures and practices, such as using micro-segmentation, multi-factor authentication, device compliance, and risk-based policies. These examples help organizations apply Zero Trust principles in their specific contexts. (nist.gov)Tier Attributes in CSF Implementation Tiers
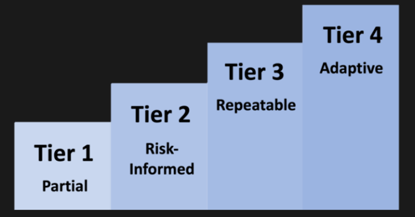
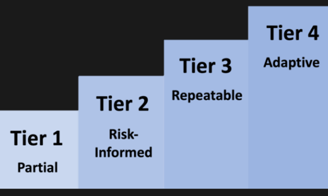
CSF 2.0 introduces Tier attributes within the CSF Implementation Tiers, which describe the level of maturity and sophistication of an organization’s cybersecurity capabilities. These attributes allow organizations to assess their current and desired state of Zero Trust implementation and compare progress and performance with other stakeholders. (cybersaint.io and nist.gov)Tier 1: Partial
Organizations at this level exhibit ad hoc and reactive approaches to cybersecurity. Their systems are not fully integrated, and cybersecurity efforts may be inconsistent or siloed across different areas.
Tier 2: Risk Informed
Organizations at this stage have begun to formalize their cybersecurity processes. There is a more consistent approach to managing risks, but these practices are still maturing and may not be uniformly applied across the organization.Tier 3: Repeatable
At Tier 3, organizations have established comprehensive cybersecurity practices that are applied consistently across the organization. These practices are proactive and include regular monitoring and review, ensuring continuous improvement.
Tier 4: Adaptive
Organizations at Tier 4 are highly advanced, with cybersecurity practices fully integrated into every aspect of their business strategy. They are continuously evolving and adapting to emerging threats, leveraging sophisticated technologies and strategies like Zero Trust to manage risk effectively.
Profile Prioritization
Another new element in CSF 2.0 is Profile Prioritization, which provides guidance on how to prioritize the Subcategories within a Profile based on an organization’s risk appetite and business needs. This helps organizations focus on the most impactful outcomes for achieving Zero Trust and ensures resources are allocated efficiently. (nist.gov)
These updates highlight how CSF 2.0 is evolving and adapting to align with modern cybersecurity needs, making it compatible with Zero Trust principles. The framework continues to provide organizations with a comprehensive approach to strengthening their cybersecurity posture, combining strategic governance with cutting-edge security models.
NIST CSF 2.0: A Roadmap for the Future
As organizations move forward with implementing NIST CSF 2.0, they will need to build strong governance structures that support the Govern function. This includes creating effective risk management strategies, defining roles and responsibilities, and ensuring that policies align with the organization’s overall goals.
For cybersecurity professionals, whether new to the field or seasoned veterans, the inclusion of the Govern function represents a shift toward a more strategic, risk-based approach to cybersecurity. It challenges organizations to see cybersecurity not just as a set of technical measures but as an essential part of business governance.
The evolution of the NIST Cybersecurity Framework, from its inception a decade ago to the inclusion of the Govern function in CSF 2.0, demonstrates a growing understanding of cybersecurity as a critical element of organizational resilience. Integrating governance helps organizations better manage cybersecurity risks and ensures that their strategies remain proactive and aligned with broader strategic objectives. This evolution is crucial for organizations seeking to navigate an increasingly complex and perilous digital landscape.
