The Cyber Kill Chain: A Framework for Defending Against Cyber Attacks
Understanding the Attack Process and How to Defend Against It
THREAT DETECTION AND RESPONSEFRAMEWORK

The Cyber Kill Chain is a framework that breaks down the stages of a cyberattack, offering a clear path from the initial stages of gathering intelligence to the final execution of an attack. This model, developed by Lockheed Martin, a global leader in defense, aerospace, and technology, is critical for understanding how cybercriminals operate and how organizations can defend themselves against increasingly sophisticated threats. Understanding each phase of the kill chain enables security teams to anticipate an attacker’s next move and take appropriate countermeasures at each step.
The Stages of the Cyber Kill Chain
The Cyber Kill Chain consists of seven stages, each representing a step an attacker typically follows when conducting a cyberattack:
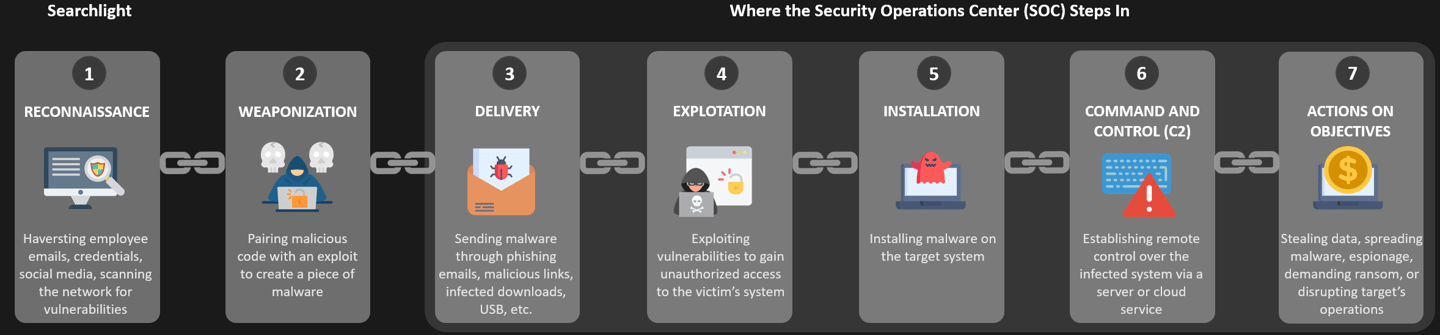
1. Reconnaissance:
During the reconnaissance phase, attackers gather critical information about the target. This can involve researching the target organization’s network, employees, and vulnerabilities using publicly available sources. Cybercriminals may use social media, websites, and domain information to gain a better understanding of their target.
Case Study: In the case of the Target breach (2013), the attackers likely obtained valuable data from a third-party vendor, allowing them to identify weaknesses in Target’s network.


2. Weaponization:
Once attackers have the necessary intelligence, they weaponize it. This could mean crafting a custom malware payload tailored to exploit a specific vulnerability identified during reconnaissance. The weaponization phase is when the attacker prepares the tools needed to carry out the attack.
Case Study: Stuxnet, a highly sophisticated worm discovered in 2010, targeted Iran’s nuclear facilities by exploiting vulnerabilities in Siemens industrial control systems, and was specifically designed to disrupt critical infrastructure.


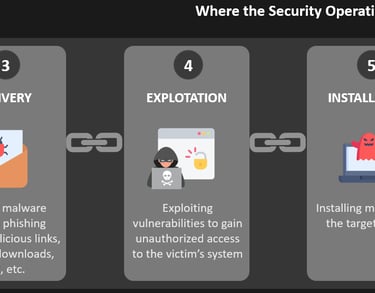
3. Delivery:
The weaponized malware is then delivered to the target. This can happen via several methods, such as phishing emails, infected USB drives, or malicious websites. The goal is to get the malware onto the target’s system in a way that bypasses security measures.
Case Study: In the Equifax breach (2017), attackers exploited a vulnerability in Apache Struts to deliver a malicious payload to Equifax’s systems, leading to a massive data breach.
4. Exploitation:
After the malware is delivered, it exploits a vulnerability in the system to gain access. This phase often involves exploiting known flaws in software or hardware that have not been patched or properly secured.
Case Study: The WannaCry ransomware attack (2017) exploited a vulnerability in Microsoft’s SMB protocol, which had not been patched by many organizations, allowing the malware to spread rapidly across the globe.


5. Installation:
Once access is gained, the attacker installs malicious software that ensures continued access to the target system. This could involve setting up a backdoor, installing rootkits, or other tools to maintain persistence on the compromised system.
Case Study: The NotPetya ransomware attack (2017) installed a backdoor that allowed attackers to maintain control and spread the malware throughout networks, even after the initial infection.


6. Command and Control (C2):
In this phase, the attacker establishes a command-and-control channel with the compromised system. This allows the attacker to issue commands, control the infected machine remotely, and often exfiltrate sensitive data or deploy further attacks.
Case Study: In the Sony Pictures hack (2014), the attackers used C2 infrastructure to control the systems remotely and deploy ransomware, while also stealing sensitive data.


7. Actions on Objectives:
Finally, the attacker executes their main objectives, whether it’s stealing data, disrupting operations, deploying ransomware, or gaining a financial benefit. This phase represents the culmination of the attack, where the attacker’s goal is achieved.
Case Study: The WannaCry ransomware attack effectively locked users out of their systems and demanded a ransom, severely disrupting operations for several large organizations, including the UK's NHS.



Recent Real-World Examples of Cyber Attacks
In recent years, there have been several significant cyberattacks that illustrate the Cyber Kill Chain in action.
Below are some notable cyberattacks from recent years, illustrating different stages of the kill chain:
Japan Airlines Cyberattack (December 2024):
In December 2024, Japan Airlines (JAL) experienced a cyberattack that disrupted over 20 domestic flights during the busy year-end holiday season. The attackers targeted the airline’s network, overwhelming it with data and causing delays. Fortunately, the attack did not affect flight safety or customer data, but it underscores the importance of robust cybersecurity measures in the aviation industry.
This attack highlights the vulnerabilities of critical infrastructure during peak times and demonstrates the need for rapid detection and response. (Source)MOVEit Transfer Software Breach (June 2023):
In June 2023, a vulnerability in MOVEit Transfer software was exploited, affecting thousands of organizations and exposing data from over 100 million individuals. Attackers used SQL injection techniques to breach the system and steal files. Victims included major organizations such as the BBC, British Airways, and the U.S. Department of Energy. This breach emphasizes the need for ongoing software updates and effective security for file transfer systems. (Source)Boeing Ransomware Attack (October 2023):
Boeing, one of the world’s largest aerospace manufacturers, fell victim to a ransomware attack in October 2023. The attackers, linked to the LockBit group, exploited a vulnerability in Citrix software. They stole over 43 gigabytes of data and demanded a ransom. The attack disrupted Boeing’s parts and distribution business, underscoring the importance of securing supply chains and sensitive data in the aerospace and defense sectors. (Source)U.S. Healthcare Sector Cybersecurity Challenges (December 2024):
The U.S. healthcare sector is grappling with rising cyberattacks, and lawmakers have proposed stricter cybersecurity rules in response. A bipartisan Senate bill aims to strengthen the cybersecurity posture of healthcare organizations by mandating measures like multifactor authentication and regular audits. This comes after several incidents of cyberattacks that have disrupted healthcare services and compromised sensitive patient data, highlighting the vulnerability of the healthcare industry to cyber threats. (Source)

How the Kill Chain Framework Strengthens Cybersecurity
Understanding each phase of the Cyber Kill Chain is essential for building an effective cybersecurity strategy. By recognizing the stages of an attack, organizations can take proactive measures to detect, respond to, and block threats before they cause significant damage. Here's why understanding each phase is important:
Early Detection: Identifying an attack during the early stages, such as reconnaissance or delivery, gives organizations the opportunity to block or mitigate the threat before it progresses.
Targeted Defense: Knowing the steps of an attack allows organizations to deploy specialized defenses for each stage. For instance, using email filtering to block phishing attempts during delivery or applying patch management strategies to prevent exploitation.
Incident Response: With a clear understanding of the Cyber Kill Chain, security teams can respond faster and more effectively. Knowing which stage of the kill chain the attack is in helps focus incident response efforts on the right areas.
Shifting Left in the Cyber Kill Chain
In recent years, cybersecurity experts have advocated for "shifting left" in the Cyber Kill Chain, a strategy aimed at detecting and mitigating threats earlier in the process. Rather than waiting for an attack to reach the exploitation or installation stages, shifting left focuses on detecting reconnaissance, weaponization, and delivery activities.
By focusing on early detection, organizations can significantly reduce the likelihood of successful attacks. Measures such as proactive vulnerability management, employee training, threat intelligence sharing, and continuous monitoring of network traffic are all part of a shift-left strategy that can disrupt an attack before it escalates to more dangerous stages.
Key Takeways
The Cyber Kill Chain provides a valuable framework for understanding how cyberattacks unfold, allowing organizations to anticipate and respond to threats effectively. By understanding each phase of the kill chain and implementing proactive defenses, businesses can better protect themselves against the growing landscape of cyber threats. Shifting left to detect and stop attacks earlier, combined with a thorough understanding of the Cyber Kill Chain, offers a powerful approach to improving cybersecurity resilience.
