SAML, OpenID Connect, and OAuth: Different keys for different identity needs
IDENTITY SECURITY

If you’ve ever wondered why your SSO uses SAML, your APIs use OAuth, and your mobile app talks about OpenID Connect, you’re not alone.
These protocols often get mixed up, and that confusion leads to bad architecture and real security problems.
Let’s simplify!
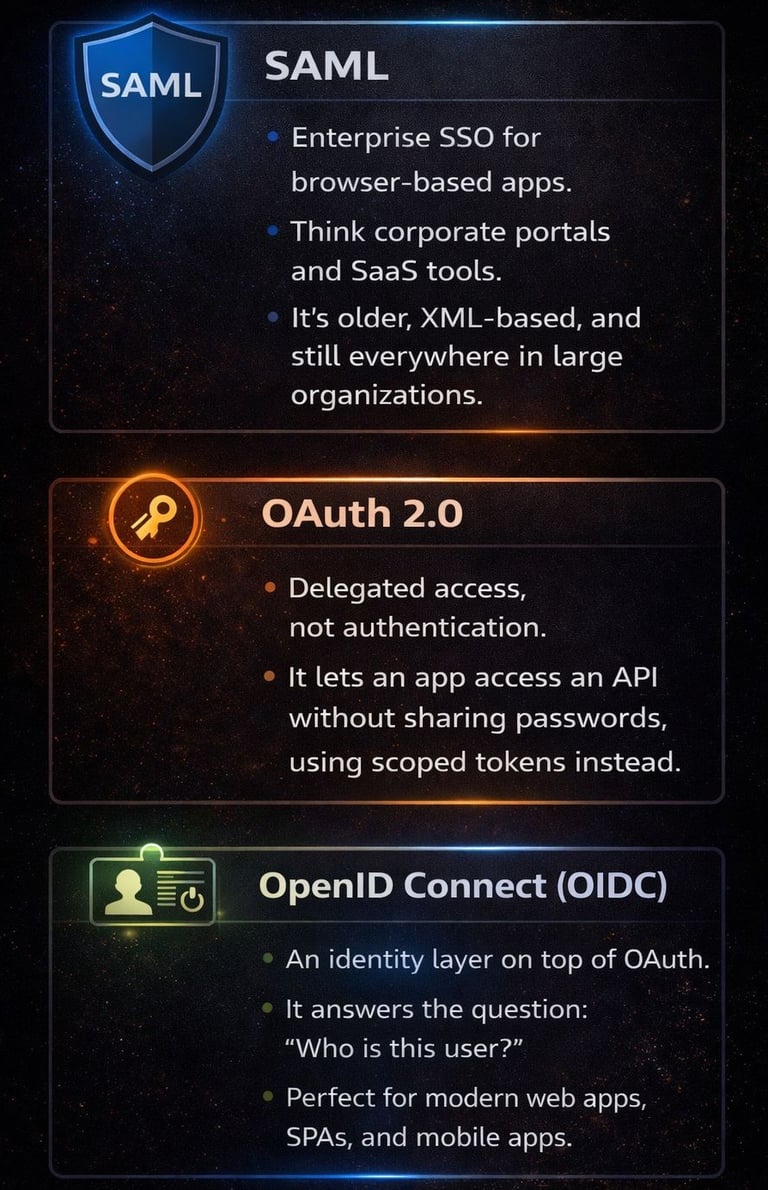
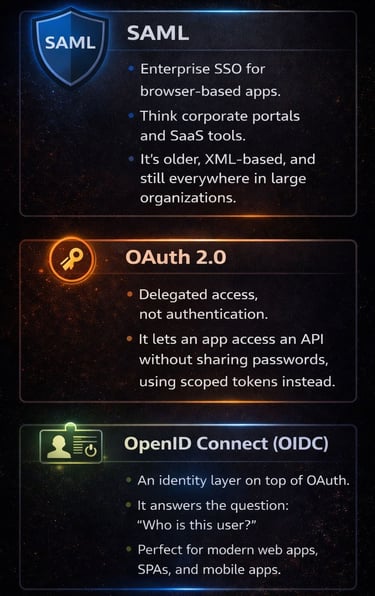
What each protocol is actually meant to do
Although they’re often mentioned together, Security Assertion Markup Language (SAML), OpenID Connect, and OAuth were designed to solve very different problems.
Which keys unlock which doors? See them in action:
SAML - the classic enterprise key: Use it for Single Sign-On (SSO) in legacy-friendly and browser-based apps. Works when logging into your corporate email, internal portals like Workday or Salesforce, and others.
📌 Behind the scenes: the Identity Provider sends a signed SAML assertion (in XML format) confirming “this user is authenticated and belongs to these groups.”
OpenID Connect (OIDC) - the modern login key: Use it when applications need login plus portable user identity. Perfect for Single-Page Applications (SPAs), mobile apps, and API-driven platforms. Signing in through Google, Microsoft, or Okta lets the app know who you are and personalize your experience.
📌 Behind the scenes: the app receives an ID token (Jason Web Token) that confirms who the user is (identity, profile claims)
OAuth 2.0 - the API access key: Use it for delegated API access and service-to-service communication. For example, it let apps access your Google Calendar, GitHub repos, or social media accounts, or Azure resources via an App Registration using a secure token, without ever sharing your password.
📌 Behind the scenes: the app gets an access token that confirms what it’s allowed to do (scopes, permissions).
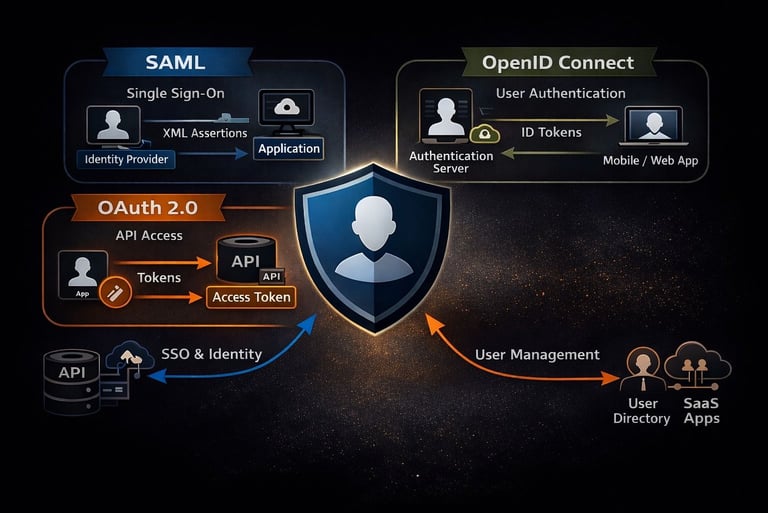
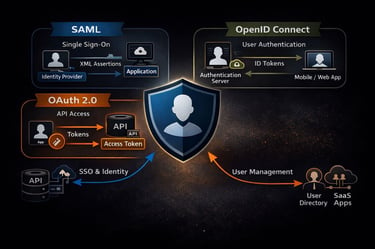
High-level workflow
Use the right key, and everyone gets in easily. Use the wrong one, and you’re left banging on the door.
Picking the right identity protocol helps you avoid messy logins, over-permissioned access, and frustrated users. It also makes your apps easier to scale, more secure, and simpler to maintain, turning identity from a headache into an enabler.


